Beware of your HP printers. They are hackable.
Finland-based security consultancy F-Secure on Tuesday announced the discovery of vulnerabilities affecting more than 150 different HP multifunction printer (MFP) products. HP has since issued patches for these vulnerabilities, essentially improving the security of a significant portion of its MFP units.
Still, now might be a good time for businesses and consumers to reassess the security of their existing printers and consider actions to avoid hacking fallout. For those in need of new printers, the holiday shopping season might provide some good pricing deals.
Considering HP’s status as a leading provider of MFPs, with an estimated 40 percent of the hardware peripheral market, many companies throughout the globe are likely using vulnerable devices, according to the F-Secure report.
Attackers can exploit the vulnerabilities to seize control of devices, steal information, and further infiltrate networks to inflict other types of damage, according to F-Secure’s research.
F-Secure security consultants Timo Hirvonen and Alexander Bolshev discovered exposed physical access port vulnerabilities (CVE-2021-39237) and font parsing vulnerabilities (CVE-2021-39238) in HP’s MFP M725z — part of HP’s FutureSmart line of printers. Security advisories published by HP list over 150 different products affected by the vulnerabilities.
“It is easy to forget that modern MFPs are fully-functional computers that threat actors can compromise just like other workstations and endpoints. And just like other endpoints, attackers can leverage a compromised device to damage an organization’s infrastructure and operations,” according to Hirvonen.
Experienced threat actors see unsecured devices as opportunities. So organizations that do not prioritize securing their MFPs like other endpoints leave themselves exposed to attacks like the ones documented in our research, he explained.
Academic Research Led to Discovery
Initially, professional development motivated the research into printer hacking, according to Hirvonem. The two F-Secure security consultants wanted to work together on a hardware hacking project to learn more about it.
While HP did a good job securing the MFP in some ways, it only took Bolshev a few hours to find the two exposed physical ports that grant full access to the device. The research expanded to place greater emphasis on stealth to develop some new tools and insights for use in red teaming and similar activities, he noted.
“These vulnerabilities affect only HP printers and the models listed in HP’s Security Bulletins,” Bolshev told TechNewsWorld.
Analyzing the Attack Vector
The most effective attack method involves tricking a user from a targeted organization into visiting a malicious website. That exposes the organization’s vulnerable MFP to what is known as a cross-site printing attack.
The website would automatically and remotely print a document containing a maliciously-crafted font on the vulnerable MFP. This, in turn, would give the attacker code execution rights on the device.
An attacker with these code execution rights could silently steal any information ran or cached through the MFP. This includes documents that are printed, scanned, or faxed. But it also impacts information like passwords and login credentials that connect the device to the rest of the network.
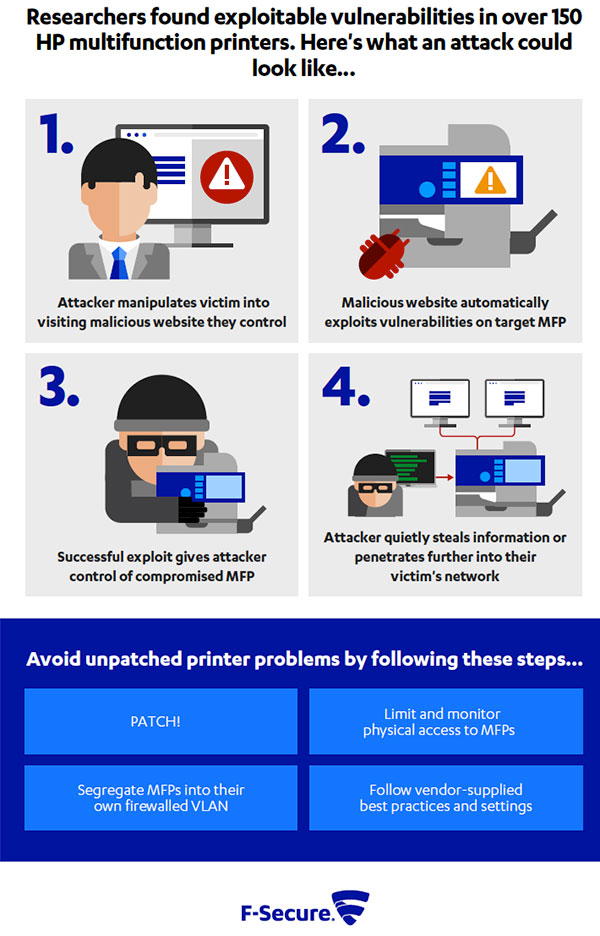
Attackers could also use compromised MFPs as a beachhead to penetrate further into an organization’s network in pursuit of other objectives. These could include stealing or changing other data or spreading ransomware.
The researchers determined that exploiting the vulnerabilities is difficult to prevent many low-skilled attackers from using them. But experienced threat actors could make use of them in more targeted operations, based on the F-Secure report.
Researchers discovered the font parsing vulnerabilities are wormable. This means attackers could create self-propagating malware that automatically compromises affected MFPs. Then the compromise spreads to other vulnerable units on the same network.
Advice for Securing MFPs
Hirvonen and Bolshev contacted HP last spring with their findings and worked with the company to patch the vulnerabilities. HP has now published firmware updates and security advisories for the affected devices.
While the attack’s difficulty makes it impractical for some threat actors, the researchers say that it is important for organizations targeted by advanced attacks to secure their vulnerable MFPs.
In addition to patching, measures for securing MFPs include:
- Limiting physical access to MFPs
- Segregating MFPs in a separate, firewalled VLAN
- Using anti-tamper stickers to signal physical tampering with devices
- Following vendors’ best practices for preventing unauthorized modifications to security settings
- Placing MFPs in CCTV-monitored areas to record any physical usage of hacked devices at the time it was compromised
“Large enterprises, companies working in critical sectors, and other organizations facing highly-skilled, well-resourced attackers need to take this seriously. There is no need to panic, but they should assess their exposure so they are prepared for these attacks,” said Hirvonen.
“The attack is advanced but it can be mitigated with the basics: network segmentation, patch management, and security hardening,” he noted.
A detailed technical write-up of the research is available on F-Secure Labs.
Patching Not Automatic
HP is not issuing pushing firmware updates over the air. Therefore, ensuring printer firmware updates is advisable to prevent any actual hacking attempts in the wild.
“We have no evidence or reports of threat actors exploiting these vulnerabilities in attacks,” cautioned Bolshev.
Consumers and IT workers must manually ensure that their HP hardware is patched. They must download and apply the HP patches manually, he said.
Another option, he added, is to use HP Web Jetadmin to update the firmware remotely for multiple printers at one time.
Better Safe Than Sorry
A skilled attacker could successfully exploit the physical ports in a little over five minutes, according to Bolshev. Executing the attack that exploits the font parser would only take a few seconds.
“However, these are not low-hanging fruits that would be obvious to many threat actors. The font parsing issue is not the easiest to find or exploit. And anything requiring physical access poses logistical barriers for threat actors to overcome,” he clarified.
The vulnerabilities date back to at least 2013 and affect over 150 of HP printer models. So many companies are likely using vulnerable MFPs.
“However, because the exploit requires a reasonably skilled attacker, smaller organizations should not panic. But larger organizations facing well-resourced/highly-skilled threat actors, and/or organizations involved in critical sectors should consider this a realistic attack vector,” concluded Bolshev.























































