Nearly half a million Covid-related domains have been created over the last two years, many of them being used by online fraudsters and hucksters.
The pandemic has created an environment in which bad actors make use of a range of Covid-related “hooks” to commit cybercrime and fraud, impacting consumers and brands, explained CSC, a domain registrar that released a study Tuesday of more than 478,000 domain names tied to pandemic keywords.
Over the study period, the report noted, the range of entities taking advantage of the growth in awareness of Covid to create websites to attract traffic and generate revenue has spiked. At the same time, the surge in sites has resulted in a larger pool of suspicious and malicious domain registrations.
“It’s insane the amount of fraud and fake goods that we’ve seen associated with these 478,000 domain names,” declared CSC CTO Ihab Shraim.
“The pandemic is an endless money-printing machine for these malicious actors,” he told TechNewsWorld.
“They’re all using this pandemic to make some serious revenue off it,” he added. “They’re making millions of dollars per month.”
Exploiting Brands
The report acknowledged that some Covid-related domain registration activity could be related to domain speculators trying to cash in on a potential hot domain name, but there were also signs of malicious third-party operations.
For example, the domains exploiting brand names related to Covid, such as Pfizer, Moderna, and Johnson & Johnson, used the same infrastructure as previously identified with harmful websites. In addition, some sites used tactics favored by bad actors to disguise, then launch attacks, such as domain parking and pay-per-click.
The report also noted that of the domains exploiting brand names, about half contained no content, while the other half were involved in pay-per-click or other kinds of advertising schemes.
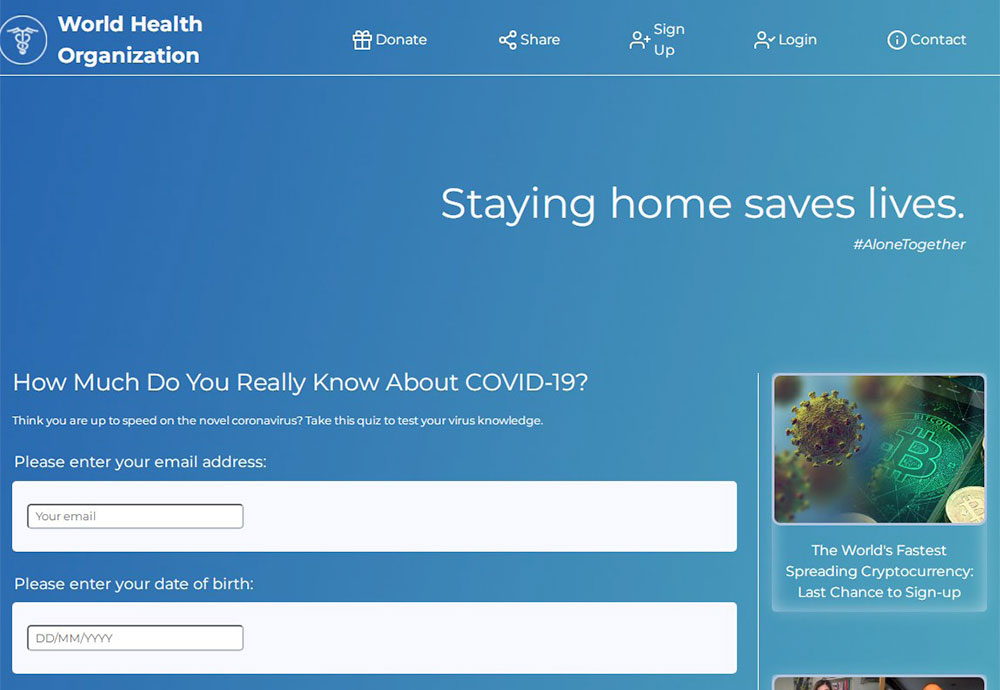
This site is branded as the World Health Organization, but the logo is wrong, and none of the social media links at the bottom of the page nor the menu options at the top are functioning. This appears most likely to be a phishing page intended to gather personal information. (Credit: CSC)
It added that a third of the dormant sites contained active MX records, which could be used as a future launchpad for malicious activity.
“Domain names are valuable to threat actors looking to capitalize on newsworthy events, especially those that involve fear or financial motivations,” observed Chris Clements, vice president of solutions architecture at Cerberus Sentinel, a cybersecurity consulting and penetration testing company in Scottsdale, Ariz.
“The reason is quite simple,” he told TechNewsWorld. “The more legitimate they can make their fraudulent sending emails or websites appear, the more likely they are to fool their victims into trusting them.”
“This trust gives them much higher odds of stealing sensitive information or money from their targets,” he added.
Confusing Domains
Moreover, domain names can be confusing to a lot of people, noted Erich Kron, a security awareness advocate at KnowBe4, a security awareness training provider in Clearwater, Fla.
“The domain name KnowBe4.com is different than KnowBe4.net or even Know-Be4.com, a difference that cybercriminals take advantage of, knowing that many people do not understand that they are different,” he told TechNewsWorld. “This allows these scammers to fake websites easily and in ways that look genuine.”
“Covid-19 is a great topic for cybercriminals because of the constant newsworthy stories and developments,” he said.
“With each development,” he continued, “there is guidance released and often revised, making it very easy to use these stories as a lure to get people to go to malicious websites or open infected documents purporting to be updated guidance or new findings in the battle against the virus.”
“Shortages of tests and vaccines are also powerful topics to get people to take action,” he observed.
“Any time there is a high-visibility incident, attackers will use that to create lures to entice victims,” added John Bambenek, a principal threat hunter at Netenrich, an IT and digital security operations company in San Jose, Calif.
“I’m sure once the shooting starts in Ukraine, the lures will shift to that very quickly,” he told TechNewsWorld.
Domain Ecosystem Problems
Bambenek maintained that the fundamental problem with the current domain system is that many registrars and companies in the domain ecosystem are willing to look the other way while they accept money from criminals to use their services to commit crimes.
“Once the U.S. relinquished control of this system,” he said, “there was no longer any pretending that it would be operated as a public benefit.”
Kron explained that problems with the domain system are largely due to the simplicity and low cost of registering domain names.
“There is little to no verification of domain names, even those using keywords related to Covid and the pandemic, or even corporations such as vaccine manufacturers, to ensure that ownership can be traced to an individual or organization,” he said.
“Essentially,” he continued, “anybody can register nearly any domain name in minutes and with no accountability.”
“Cybercriminals have perfected the technique of registering domain names with very little effort and cost, often knowing that the domain would last 48 hours or less,” he added.
Cloud computing has added to the problem, asserted Brian Johnson, CSO at Armorblox, an enterprise communications protection provider in Sunnyvale, Calif. “Phishing and business email compromise attacks that use these ‘in the moment,’ fleeting domains cannot be detected by existing security tools,” he told TechNewsWorld.
What’s more, domains can be susceptible to a number of attacks, added Sanjay Raja, vice president of Gurucul, a threat intelligence company in El Segundo, Calif.
“Threat actors can take advantage of expired domains, problems with SSL certificates, poor security controls at domain registrars, domain extensions that are actually registered by threat actors but look legitimate and domain hijacking through phishing attacks or other credential-stealing methods,” he told TechNewsWorld.
“These are just some of the tactics used that eventually lead to presenting users with domains that allow for compromising networks and installing and executing malware or ransomware,” he said.
High Marketplace Activity
Other areas covered by the report included e-commerce, mobile apps, phishing, and social media.
The pandemic saw the appearance of very high volumes of Covid-related marketplace activity, it noted. Many of those listings were for counterfeit or otherwise low-quality or ineffective products, appearing in response to unprecedented consumer demand.
In the mobile domain, Covid-related apps found in the main apps stores were legitimate, CSC reported, but a significant number of programs found outside the stores were malicious.
The report also noted that Covid-related phishing campaigns contained a number of content types, including emails driving users to websites intended to harvest personal details, distributing malicious software through attachments, and directly soliciting financial donations.
In a similar vein, fake profiles on social media were used to direct users to phishing sites or solicit donations. In addition, pages on those sites were used to feature e-commerce content of dubious quality, offer app-based trackers with malicious payloads, and spread disinformation.

























































