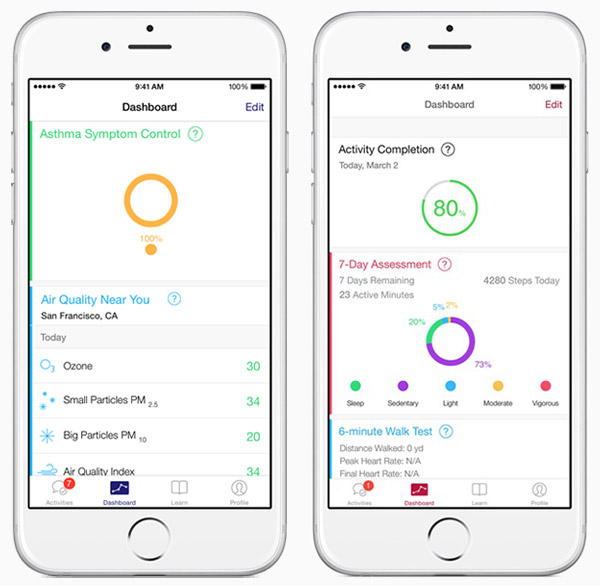
Apple earlier this week announced ResearchKit, an open source framework that will let medical and health researchers gather data through iPhone apps. ResearchKit will be released in April.
Apps to monitor asthma patients and for studies on breast cancer survivors, cardiovascular health and Parkinson’s Disease, already have been developed using ResearchKit.
The demand for remote patient-monitoring is skyrocketing. [*Correction – April 22, 2015]
Wearable devices will boost the healthcare-related market, said Danielle Levitas, a group VP at IDC, in an earlier conversation on this topic.
Apple would push “something that’s hardware-related,” she told TechNewsWorld, that would “demonstrate its various healthcare partnerships and related software and services.”
In fact, Apple “needs to focus on health and lifestyle — not activity — to expand the relevance of wearables beyond the fitness audience,” ABI Research Senior Practice Director Nick Spencer told TechNewsWorld in an earlier interview.
Global Sharing
The framework has specific activity modules such as memory and gait testing, to which researchers can contribute. They can share their data with the global research community.
ResearchKit apps are available now in the App Store for residents of the United States. They will be rolled out to other countries later.
The apps run on the iPhone 5, 5s, 6, 6 Plus, and the latest-generation iPod touch.
ResearchKit Limitations
Apps developed with ResearchKit will apply only to a small universe — iPhone users, who tend to be wealthier and better educated than the rest of the population.
Further, it’s unlikely that all iPhone users will be comfortable using an app to monitor their health or to send their health data to a third party.
“You can collect a massive amount of data very quickly across a broad sampling of users,” said Rob Enderle, principal analyst at the Enderle Group.
However, “the collection process isn’t statistically valid. A self-selecting sample like this one isn’t representative of a population,” he told TechNewsWorld.
Security and iApps
Apple says, in essence, that personally identifiable data gathered using ResearchKit will not be at risk, but security is likely to be a major issue.
Mobile security is generally poor, and intelligence agencies and law enforcement have little compunction about seizing or conducting surveillance on mobile devices both in the U.S. and abroad. The CIA for years has been trying to crack iOS security.
Meanwhile, there have been repeated hacks of iOS, and the OS itself is not secure — Apple had to patch 24 vulnerabilities in its iOS 7.1 update.
Security researcher Jonathan Zdziarski in July disclosed a list of iOS vulnerabilities that was shocking.
Among them were undocumented services that bypassed backup encryption and could be accessed both through USB ports and wirelessly. They offered access to all data encrypted with data protection if the iOS device were not rebooted since the last entry of the user’s PIN. The services included a packet sniffer that could be monitored remotely over WiFi.
Further, smartphones themselves are not secure, as they broadcast personal information to app developers.
ResearchKit can request access to an iPhone’s accelerometer, microphone, gyroscope and GPS sensors to monitor patients.
Danger, Danger!
The healthcare sector is not prepared for the new cyberage, ABI Research has found.
The value of personal health information is 10 times that of financial data; medical identity theft and fraud are increasing; and there have been hundreds of instances of data breaches at healthcare providers, with the loss of millions of personal records.
However, the healthcare industry spends very little on cybersecurity compared to other regulated critical industries.
“If the data resides on the phone at all, it won’t be secure enough,” Enderle said.
Still, “one of the best ways to secure user data is not to collect it in the first place,” Tripwire Senior Security Researcher Ken Westin told TechNewsWorld. “The second way to secure data is to encrypt it and ensure the keys stay safe.”
*ECT News Network editor’s note – April 22, 2015: Our original published version of this story stated that the app market was projected to reach 26 billion users, according to Sagentia. After a reader called that statistic into question, TechNewsWorld on April 17 removed the reference, pending clarification from MIT Technology Review, which originally had published the projection. Anne Stuart, editor, custom editorial content, MIT Technology Review, on April 21 responded to our query, informing TechNewsWorld that the projection was incorrect and should have read, “the market for mobile medical apps will reach $26 billion by 2017.” Stuart also pointed out that the article was “content created for an advertiser” (Sagentia). The MIT Technology Review updated its piece, Stuart also said, and included a reference to the original source for the stat (Research2Guidance), which had been missing from the Review’s original article. However, as of 4-22-2015, the Review had not published any correction notification to accompany the change. TechNewsWorld decided to leave the reference out of our article, apart from this explanation for the substantive change in our content.